Even before the coronavirus phenomenon, the unfortunate reality is that there has never been an environment more conducive to fraud than there is today due to the way the internet and technology have established sophisticated new tools for fraudsters to use. The coronavirus pandemic, with the fear and anxiety of the public coupled with a large amount of federal funding available, makes this environment significantly more challenging in the fight against fraud.
Stolen digital information accelerates and enables fraud. This simple truth is we need to change the way organizations think about protecting themselves from fraudsters. A recent example drives this point home. Ridesharing has become part of our daily life — Uber and Lyft are ubiquitous across the U.S. and abroad. In a recent scheme, a fraudster would order a ride and then contact the driver via phone, which passengers get access to once a ride is hailed. The fraudster spoofed the calling number to make it look like it came from the rideshare headquarters. When the driver answered, the fraudster would tell them to cancel their ride with “Mark,” which the driver recognized as the passenger’s name, and pull over. Most drivers, seeing the phone number and the fact that the caller knew the name of the passenger that they were about to pick up, immediately complied. The fraudster would then walk the driver through an exhaustive review of the billing settings, eventually telling the driver that money was not getting deposited correctly and directing them to input a new account number, which the fraudster provided. The drivers, assuming they would not be paid otherwise, were happy to input the new number. All future funds for those drivers were then funneled to an offshore account.

Stolen data, sold on the dark web, provides fraudsters sought-after credibility
Today, fraudsters are operating within a much broader and more complex cybercrime landscape. That’s because we live in the age of the breach. Almost daily, companies experience data breaches, most of which contain Personal Identifiable Information (PII). These PII breaches often contain critical data about a company’s constituents, partners, customers and employees. There are leaked corporate documents containing business processes, intellectual property designs and systems information. Breaches contain credentials, passwords and digital certificates.
Aside from the obvious kinetic cyber risks, data breaches pose an even bigger threat due to the fraud schemes they enable. Much of the stolen digital information ends up for sale or freely available on underground digital marketplaces. Many of these markets require special network software to access. The Onion Router (TOR) provides an anonymous vehicle to access the dark web, where marketplaces for buying and selling illicit goods — including PII — for digital currency, are numerous. There are hundreds of marketplaces on TOR and the dark web advertising billions of PII records for sale. A largely commoditized and saturated market, the sale of PII and related corporate data is inexpensive, sometimes costing just a few cents per record.
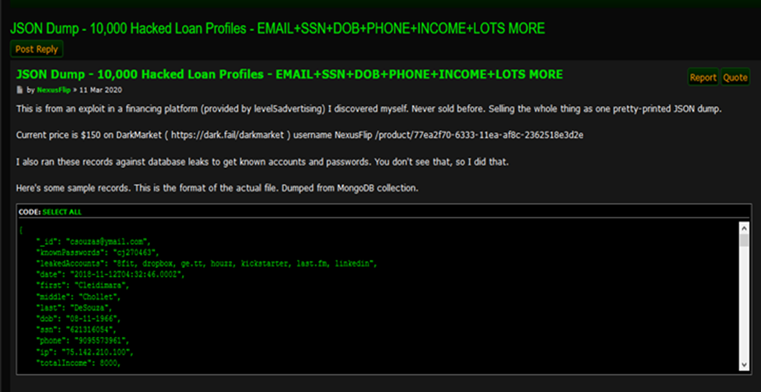
These marketplaces are already becoming a lucrative forum for fraudsters to buy and sell access to consumer, business and government information that can then be used to fraudulently apply for coronavirus stimulus benefits. The generous Small Business Administration (SBA) loan programs established under the stimulus bill are especially appealing to fraudsters. For example, one dark web seller last month was offering 10,000 stolen loan profiles for sale. The seller was originally offering the stolen profiles privately but decided to make the sale a public offering to take advantage of the current coronavirus environment, where he or she would likely be able to sell at a premium.

In addition, fraudsters are capitalizing on peoples’ eagerness to learn the latest authoritative information concerning the novel coronavirus to use new and even recycled phishing schemes. Cyberthreat intelligence firms are finding that fraudsters are dusting off their old phishing playbooks for use in the coronavirus environment. Older phishing kits that were previously deployed and then retired are being pressed back into service to target those working from home.
Cyberthreat intelligence: The war on fraud’s new front
Today, cyber intelligence providers use software to mine markets, conversations, forums and other sources looking for customer-specific data. The moment a post is made about a company, the company is notified about the post and all of the forensic data is provided. Detection of the monetization of stolen data provides many benefits to the enterprise. Notification of a potential breach from the intelligence provider — rather than a customer or the authorities — allows the enterprise to gain the upper hand to triage the situation and get in front of negative public relations outcomes. Further, if the stolen data has intrinsic cybersecurity value, the company can quickly implement countermeasures, such as locking or reissuing credentials and certificates.
The online channel, fueled by the digital crime economy on both the deep, legitimate web and the dark web, provides the tinder that enables fraud to thrive. Cybercriminals operate in a dark and underground network, but in the last few years, cyberthreat intelligence has evolved with the tools to watch them and take action before they can do real damage. Today, most large commercial enterprises have widely adopted cyberintelligence and digital risk protection programs to inform themselves of how bad actors are targeting them. Cyberthreat intelligence companies monitor the deep and dark web forums. They watch the fraudsters, interact with them on forums, sometimes obtain samples of what they are selling to further validate and inform the victim organizations about the vulnerable assets that are being exploited. Fraudsters are taking advantage of a fast-moving new technological landscape. But we can stay on top of their actions by monitoring their behavior on these forums and acting quickly to stem the damage. Educating your staff and external stakeholders about the dangers of phishing, maintaining patches and security updates to protect your infrastructure, and leveraging cyberthreat intelligence are all vital tools in the fight against cybercrime and exploitation of your organization.
By Linda Miller, CFE, Principal, Fraud Risk Management, Grant Thornton, LLP, and Kurtis Minder, CEO of GroupSense
Source: https://www.acfe.com/fraud-examiner.aspx?id=4295010517
